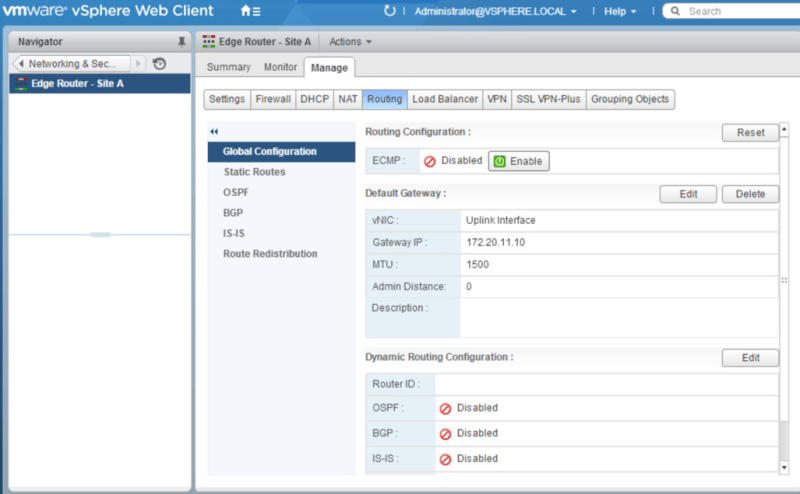
NSX Edge provides network address translation (NAT) service to assign a public address to a computer within a private network. The NSX edge supports using source NAT (SNAT) and destination NAT (DNAT). SNAT is used for translating a internal IP address to a public external address. Since external IP addresses have no knowledge of internal IP addresses, NAT is needed for communication. DNAT allows access from outside/external networks to internal private networks. NAT is important for providing access to services within your private network and for providing the ability to access services that are external to your network. For ex: In order for a machine on your private network to be able to access the internet, NAT is need. In this blog post, I’ll show you how to configure source NAT (SNAT) on a NSX edge device to do just that.
In our example, we will have a VM (VM01) with a IP address of 10.1.2.20 that is attached to a NSX logical switch (Tenant A). In order for this VM to access the internet, we will translate it’s IP to an IP that is internet accessible. Right now, as you can see, we cannot access the outside world. We test this by pinging Google’s public DNS (8.8.8.8).
Let’s get started with changing this and making the VM accessible to the internet. Read Full Article