Picking up from where we left off in our last post, we will be configuring routing between the physical network and the virtual network by means of the NSX Edge Services Gateway appliance.
A little backgroud about the NSX Edge:
NSX Edge provides network edge security and gateway services to isolate a virtualized network. The NSX Edge gateway connects isolated, stub networks to shared (uplink) networks by providing common gateway services such as DHCP, VPN, NAT, dynamic routing, and Load Balancing. Common deployments of NSX Edge include in the DMZ, VPN Extranets, and multi-tenant Cloud environments where the NSX Edge creates virtual boundaries for each tenant.
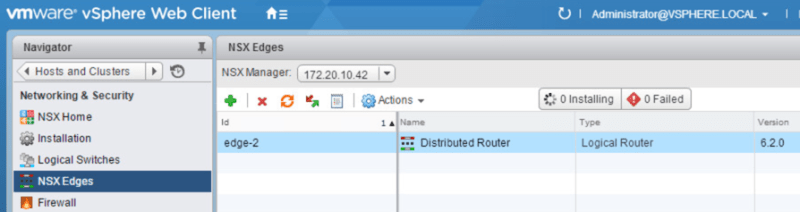
So to begin, we need to deploy a NSX edge appliance. We do this by navigating to Networking & Security > NSX Edges and clicking the green +